The usage of mobile apps has increased dramatically in recent years. According to statistics, there are 8.1 billion people around the world, and 88% of them (6.89 billion) are smartphone users. It means that the majority of people across the globe use mobile apps.
This surge has opened new doors for hackers to exploit vulnerabilities in mobile apps and steal sensitive information. Statistics show that cyberattacks on mobile apps have increased by a staggering 187% from 2022 to 2023, and fintech apps are one of the top targets of cybercriminals.
That’s because 97% of fintech apps lack basic security, 83% store data insecurely, and 80% use weak encryption protocols. These stats show that ensuring the security of sensitive data has become one of the biggest concerns for both users and app developers.
That’s where this guide comes into place. It contains the best practices that will help you ensure security for mobile apps and protect the sensitive information they handle.
Importance of Mobile Application Security

In today’s interconnected world, where mobile devices have become an integral part of our daily lives, the stakes for securing mobile applications have never been higher. Mobile apps often handle sensitive user data, ranging from personal information to financial details, making them attractive targets for cybercriminals.
Protecting User Data
Most mobile apps handle personal information, login credentials, financial details, and location data. It’s important to protect this information to prevent unauthorized access, identity theft, financial fraud, and misuse.
Mitigating Financial Risks
Mobile apps are commonly used for financial transactions like online banking and mobile payments. If an app has insufficient/poor security measures, such as weak server-side controls and storage of financial data without encryption, it’ll expose its users to security risks, which can lead to unauthorized transactions and compromised payment information.
The same happened with Capital One financial company back in 2019 when “Paige A. Thompson” stole the data of 100 million credit cards. You don’t want this to happen with your app, and the best way to ensure that is to implement strict security protocols like multi-tiered authentication, advanced data encryption, and real-time threat intelligence in order to protect users’ financial data.
Preserving Brand Reputation
A security breach in a mobile app can harm your company’s reputation by eroding user trust. Keep in mind that news of data breaches spreads quickly and can also result in legal consequences. If you want to maintain a positive brand image and enhance customer loyalty, you need to ensure your mobile app safety.
Compliance with Regulatory Standards
Different industries, like finance, healthcare, tourism, and e-commerce, have different regulatory standards regarding data security and privacy. Mobile applications operating within these sectors must comply with these standards to avoid legal penalties.
For example, GDPR, or General Data Protection Regulation, provides detailed guidelines for the collection and processing of personal information of end-users. According to this standard, companies are only allowed to retain user data for the specific purpose explicitly stated, and solely for the duration required for processing. After that, all the data that is no longer required must be erased, which minimizes the risk of unauthorized access and data breaches.
Protecting Against Reverse Engineering
Some mobile apps contain valuable intellectual property, including proprietary algorithms, trade secrets, or innovative features. An app with inadequate security will allow malicious online actors to reverse engineer the app’s code, extract valuable information, and potentially clone or pirate the app.
It can lead to devastating consequences, such as intellectual property theft, that can damage your app’s integrity and affect your overall business negatively.
Mobile App Security Best Practices
Now that you understand why mobile app security is important, let’s discuss the best practices to ensure that. In this section, we’ll explore effective strategies and protocols to fortify mobile app security to ensure a robust defence against potential threats and vulnerabilities.
Secure the Infrastructure
Most mobile apps do not operate in isolation. It’s especially true when it comes to fintech and tourism apps, as they’re usually a part of a bigger ecosystem that consists of multiple services and platforms.
They have multiple APIs integrated into them, which means sensitive information flows to and from these apps continuously. Therefore, you must implement a holistic security strategy. Otherwise, it’ll be easy for cybercriminals to intercept the data transmission flow and hack the app.
The same happened with Finastra, a digital financial institution, back in March 2020. Hackers breached the servers of this company and successfully launched ransomware. Luckily, they recovered from this attack because the data of their clients wasn’t compromised.
But it certainly doesn’t mean that every organization can recover from such an attack, and that’s why it’s important to improve the infrastructure of your app as a whole. One of the best strategies to achieve that is to use an approach called seven layers of cybersecurity.
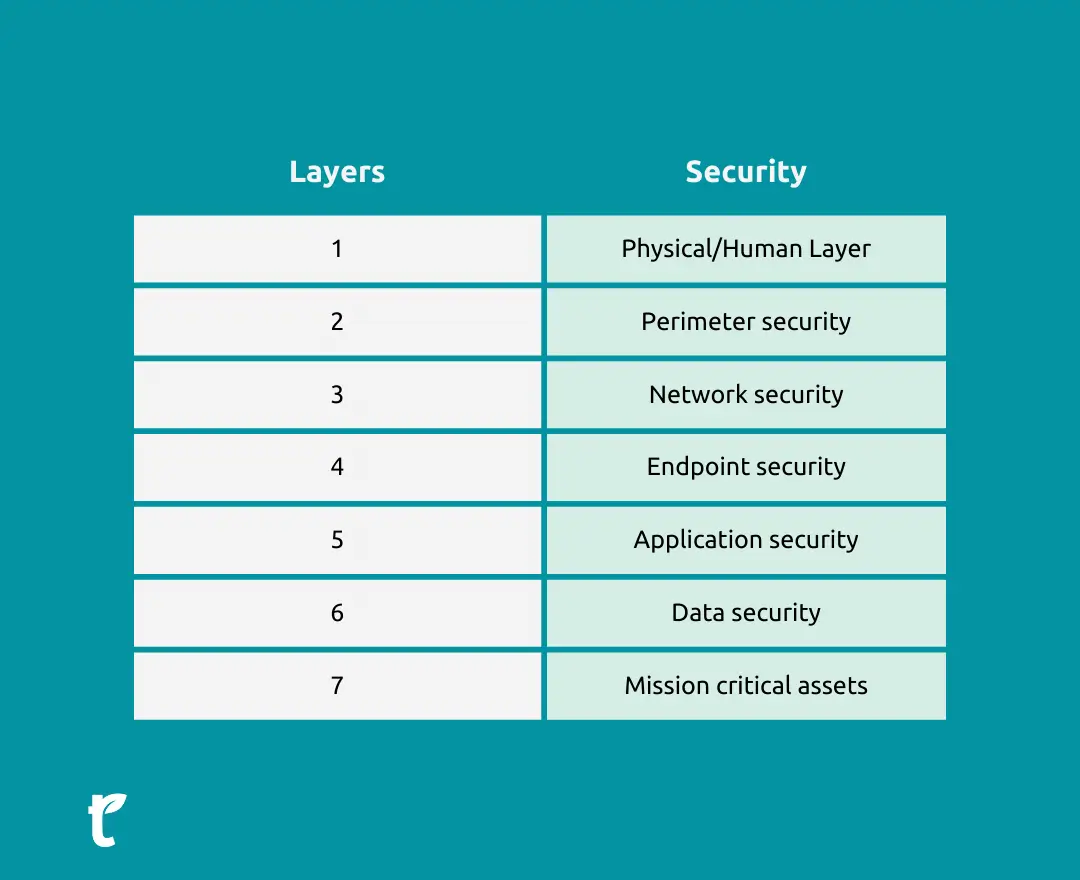
You can start by ensuring the security of your entire network’s perimeter. It’ll help you identify and stop cyberattacks and data breaches before they reach any further in the system. At this level, you can use anti-DDoS (Distributed Denial of Service) tools, proxy servers, and next-gen firewalls.
Next, you’ll need to work on protecting the application and server layer, and one of the best ways to achieve that is to install an antivirus solution in your system. It’s also equally important to update your OS (Operating System) regularly to address underlying vulnerabilities.
Additionally, make sure that you consider all the external devices (if any) connected to your network, as they can act as an endpoint for hackers to infiltrate the system. To manage this risk, you can use an endpoint management system.
Lastly, don’t forget to ask your security team to stay vigilant and act as a physical layer of security. It’s important to talk about it when hiring people or external vendors and make sure that they are up to date with the latest cybersecurity practices.
Renowned certificates not only validate individuals’ expertise but also serve as a valuable assurance for clients and partners. A team equipped with recognized certifications enhances the overall security posture of your organization, instils trust, and demonstrates a commitment to maintaining the highest standards of cybersecurity.
Follow Secure Coding Practices
Secure coding is best ensured when the hired developers possess an innate understanding of and dedication to implementing industry-standard practices. So, it is advisable to select professionals or a company with a proven track record in the field of security.
Prioritize assessing their hands-on knowledge and inquire about their commitment to integrating secure coding principles into their work. Here are the best practices that we believe make a difference:
- Input Validation: Input validation involves validating and sanitizing user input to prevent common threats like SQL injection and cross-site scripting. You need to check the validity, length, and format of user input to keep malicious data at bay and ensure security in mobile applications.
- Proper Error Handling: Proper error handling is one of the most important app security features to prevent sensitive information leakage and potential security risks. Make sure that you display user-friendly error messages but avoid revealing sensitive system details that attackers can exploit.
- Code Obfuscation: Code obfuscation techniques allow you to make the app’s code harder to understand and reverse engineer. You can use this to protect proprietary algorithms, sensitive logic, and other intellectual property from unauthorized access and theft.
- Code Review: It’s important to review your source code periodically to identify any security weaknesses or vulnerabilities. This way, you’ll be able to find and address security issues before they can be exploited.
- Regular Security Updates: Stay up to date with the latest security patches and updates for frameworks, libraries, and dependencies used in the app. It’ll help you address the weaknesses in all the third-party components of your app to keep it secure.
Ensure Compliance with Regulatory Bodies
Regulatory bodies play a critical role in ensuring the security of digital solutions, including mobile apps. They outline regulations and standards that organizations need to follow in order to protect their digital solutions from cyberattacks.
Failing to comply with these regulations not only puts your app at risk of falling victim to cyberattacks but can also lead to legal issues and fines.
While specific regulations and standards can vary from country to country, their common objective is to protect consumer and business data from cybersecurity risks.
For example, companies related to the fintech industry need to comply with the following regulations, depending on their location and business nature.
- Data Privacy Regulations: Fintech organizations need to comply with the GDPR (General Data Protection Regulation). It ensures that your app collects, stores, and processes customer data securely.
- Payment Card Industry Compliance: Fintech companies handling payment card data must comply with the PCI DSS (Payment Card Industry Data Security Standard). This standard ensures the security of payment card data and protects against unauthorized access or breaches.
- Information Security Standards: To ensure information security, fintech apps must comply with the ISO 27001 standard. It’ll help you ensure the integrity, confidentiality, and availability of the app and data it handles.
Be Extra Careful While Using Third-Party Components
When incorporating third-party components, such as libraries or APIs, into your mobile apps, be extra careful and consider the security risks they might have. Test and review their code thoroughly (if possible) before integration to identify and address vulnerabilities they contain.
You can also consider limiting the number of third-party libraries to reduce the attack surface of your app. It’ll make it easy for you to manage and maintain the app’s security.
When utilizing third-party components, make sure that your users can access the data they are allowed to. It will mitigate the risk of unauthorized access and protect your app against data breaches and reputational damage
Use Advanced Authentication Methods

Advanced authentication methods are among the best ways to protect user accounts and sensitive information. Make it mandatory for all app users to create strong passwords as per the following guidelines.
- All passwords should be at least 12 characters long, as long strings are generally more secure.
- A password should contain a combination of uppercase and lowercase letters, special characters, and numbers. It’ll increase the password’s complexity and make it harder to guess/break.
- Encourage users not to use their personal information like name, birthdate, or address in the password. That’s because such information can be easily guessed or obtained by attackers.
- No user should use common words or phrases found in the dictionary because hackers often use dictionary-based attacks to crack passwords.
- It’s important to avoid using simple patterns like “123456” or “qwerty” as they are easily guessable. Therefore, passwords should have random combinations of characters.
- Ask all the users to change their passwords periodically, ideally every 3 to 6 months. It’ll reduce the risk of an attacker gaining prolonged access to the user’s account.
Utilize the Power of MFA
Other than creating strong passwords, it’s also important to implement MFA (Multi-Factor Authentication). It’ll ask all the app users to complete an additional verification step, such as entering a unique code sent to their registered mobile device or email address, in addition to their password. Here are a few popular types of MFA that can be used.
Questions-Based Authentication
This method introduces an additional layer by posing personalized queries to users during the login process. Users are required to answer questions that only they should know, adding a dynamic and personalized element to the verification process. Questions can be based on personal information, preferences, or historical data associated with the user.
Biometric Authentication
Biometric MFA relies on unique physical or behavioral attributes for user verification. Common biometric modalities include fingerprint recognition, facial recognition, iris scanning, and voice recognition. This approach provides a high level of security as it is challenging to replicate or forge biometric traits.
TOTP (Time-Based One-Time Passwords)
TOTP is an advanced cryptographic algorithm that generates unique passwords at fixed intervals, typically every 30 seconds. Users need to enter the current one-time password generated by a TOTP-enabled application. Popular applications for TOTP include Google Authenticator, Microsoft Authenticator, and Twilio Authy.
Using MFA will add an extra barrier against unauthorized login attempts to enhance the overall security of the app.
Secure Data at Rest
The best way to secure data at rest is to implement strong encryption measures. It’ll transform the data into an unreadable format, and only authorized parties with the decryption key will be able to access it.
It’s also critical to store user databases, credentials, and other critical data in designated and controlled locations. It involves implementing access controls, like role-based access or strong authentication mechanisms, to limit who can access the stored data.
Additionally, you should also back up the encrypted data regularly and store them in a secure location to protect against data loss and corruption. You can use the following tips to implement a holistic data backup strategy.
- Regular Backups: Determine the optimal frequency for data backups based on the nature of your app’s data and the frequency of updates. Critical data may require more frequent backups to minimize potential losses.
- Incremental Vs Full Backups: Using incremental backups is a wise choice, as they only store changes made since the last backup. This can significantly reduce the time and storage space needed for each backup.
- Automated Backup Processes: Implement automated backup processes to streamline the workflow and reduce the risk of human error. Automation ensures that backups occur consistently without manual intervention.
- Secure Storage Locations: Choose secure storage locations for backups, considering both physical and cloud-based options. Ensure that access controls are in place to restrict unauthorized retrieval of sensitive data.
- Versioning: Consider implementing versioning in your backup strategy to maintain multiple iterations of data, which means keeping different versions of your data over time. It’ll enable you to roll back to a specific point in time in case of errors or data corruption.
- Regular Testing and Restoration: Periodically test the restoration process to validate the integrity of your backups. It’ll help you make sure that data can be efficiently restored whenever needed to minimize downtime in the event of data loss.
By combining encryption with a comprehensive and well-managed backup strategy, organizations can significantly reduce the risks associated with data loss, corruption, and unauthorized access. This approach not only enhances the overall resilience of data management but also aligns with best practices for maintaining the confidentiality, integrity, and availability of sensitive information.
Encrypt Source Code
Native mobile apps often contain critical code on the client side, making them vulnerable to malicious attacks. It makes it possible for hackers to get their hand on the source code, manipulate it to create a rogue app, and distribute it through unofficial app stores.
It can trick unsuspecting users into downloading compromised versions, which can damage your brand’s reputation. Additionally, attackers can also inject malicious code into your original mobile app to steal data.
To prevent these issues, you can ask your developers to encrypt source code to make it unreadable to unauthorized parties. It’ll make it almost impossible for hackers to understand the inner workings of the app and reduce the risk of reverse-engineering attacks.
Protect Data Transmission

Encryption again comes in handy when it comes to securing data transmission. You can use TLS, SSL, and HTTPS to make sure that your data is transmitted in an encrypted form between the app and the server.
Additionally, you can use a VPN service as well to create a VPN tunnel for the same purpose. A VPN tunnel is a secure and encrypted connection established over the internet between two devices or networks. It ensures that the data transmitted between them remains confidential and protected from potential eavesdropping or unauthorized access.
It’ll allow your teams to communicate securely by creating a private and secure pathway for their data to travel through, which will safeguard sensitive information from external threats.
Perform Rigorous Testing
Performing rigorous testing allows you to ensure that your app meets all specifications and adheres to security standards. So, testing should be an integral part of your mobile app security strategy.
There are different types of testing that you can perform, including penetration testing, functionality testing, and code review.
- Penetration testing allows you to identify vulnerabilities by simulating real-world attacks and attempting to exploit them.
- Functionality testing ensures that the app functions as intended and meets the desired user experience.
- Code review involves a thorough examination of the source code to identify and fix any security vulnerabilities or weaknesses that may have been missed during development.
In addition to these methods, you should also employ other testing approaches like security scanning, risk assessment, and threat modelling. These techniques will help you uncover security risks and eliminate any unrecognized malicious activities from third-party sources.
Final Words
There are billions of people around the world who rely on mobile applications for their day-to-day activities. So, regardless of the type of mobile app you develop, you need to make sure that it offers a seamless user experience and protects the sensitive data it handles.
In addition to prioritizing data protection and user experience, it’s also important to keep the human factor in mind. Ensuring the security of your mobile app involves not only robust coding practices but also the expertise of the individuals behind it. Therefore, hiring or collaborating with professionals experienced in cybersecurity is essential.
Even if you may not be a cybersecurity expert yourself, having a team with the right knowledge significantly strengthens your app’s defense against potential threats.
We hope this guide has helped you understand the importance of ensuring security in mobile apps and the best practices you can use to achieve that. Lastly, don’t forget to stay up to date about the latest cybersecurity threats on mobile apps to improve your security strategy and keep it relevant.









.webp)












